Healthcare Data Inventory Management Software
Understanding where your organization stores sensitive data is critical for reducing security risk and ensuring compliance. Accountable's Data Inventory Management feature provides a centralized hub to track and monitor every location where Electronic Protected Health Information (ePHI) and Protected Health Information (PHI) are stored.

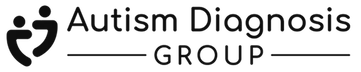





-
Identify & Assess Data Risk with Ease
By taking inventory of all data sources, including hardware, cloud storage, and vendor systems, your organization can:
-
Monitor data locations and assess risk levels for each inventory item
-
Improve security visibility by tracking data flow across systems and vendors
-
Prepare for audits by demonstrating a clear understanding of your organization's data storage and management
-
-
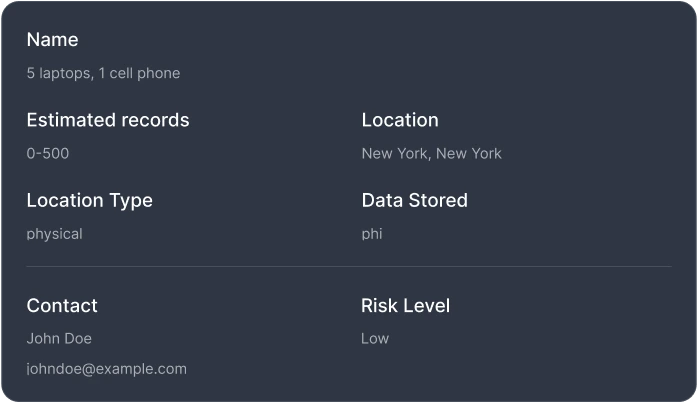
A Centralized Solution for Data Flow & Compliance
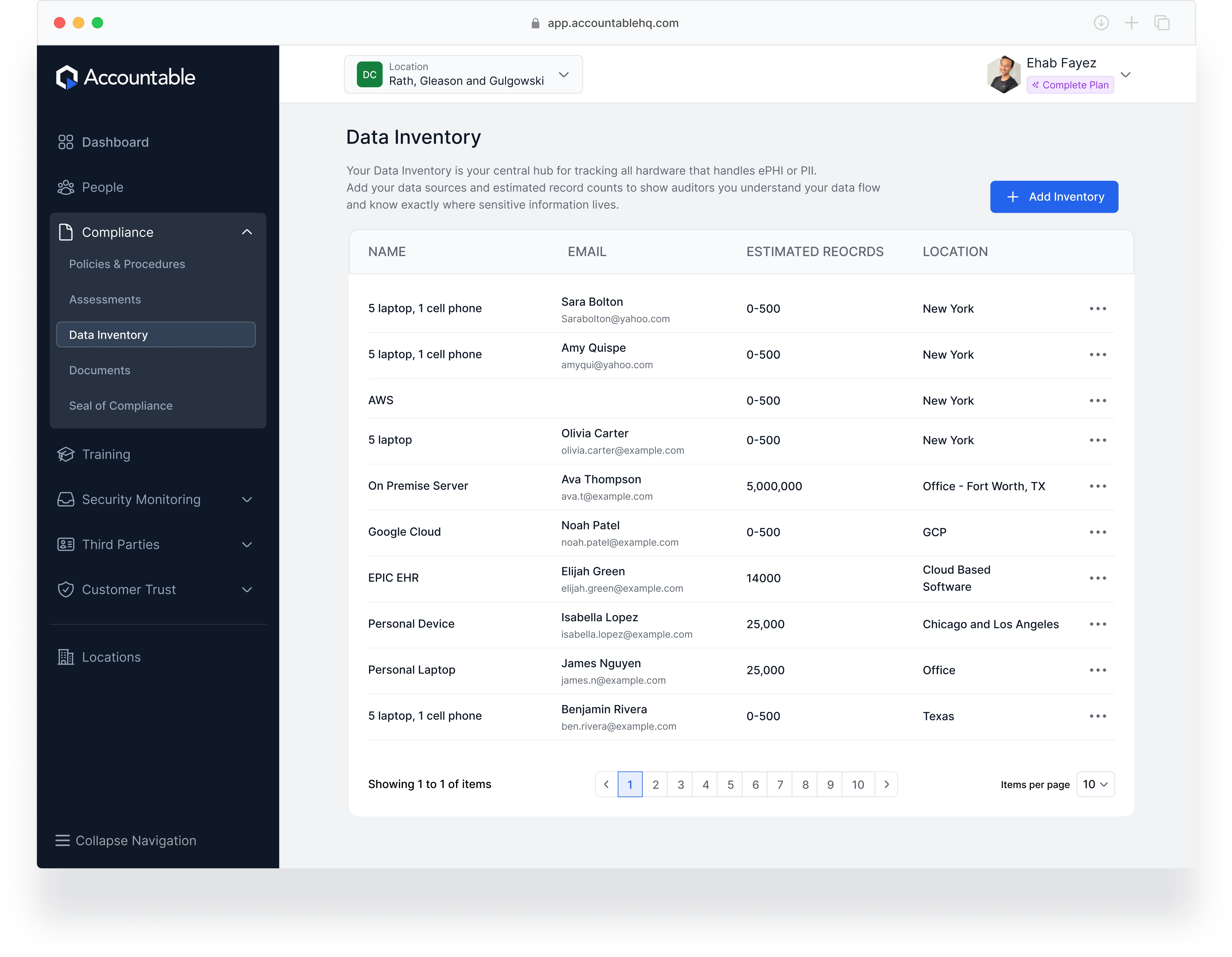
Your Data Inventory acts as a single source of truth for all business-critical information systems. Easily log where data is stored, estimate record counts, and continuously track changes. This structured approach helps ensure compliance with HIPAA and other data privacy regulations while strengthening your organization's security posture.
Stay Prepared for Audits & Compliance Reviews
Regulatory compliance requires organizations to demonstrate that they understand and manage their data flow effectively. Accountable's Data Inventory Management tool allows you to:
-
Document and categorize all data sources in one location
-
Prove compliance by showcasing structured data tracking during audits
-
Reduce risk exposure by identifying and mitigating data vulnerabilities
Features to power any privacy, security, and risk management program
Compliance
Security Risk Assessment
Identify & mitigate risks
Employee Dashboard
Monitor compliance progress
Policy Management
Centralized policy control
Data Inventory Management
Track & secure data
Policies & Procedures
Simplify compliance policies
Privacy Compliance Software
Automate privacy policies
Employee Training
HIPAA Training
Ensure HIPAA compliance
Security Awareness Training
Prevent cyber threats
Sexual Harassment Training
Foster workplace safety
Fraud, Waste, & Abuse Training
Learn best practices
Bloodborne Pathogens Training
Prevent exposure
Custom Training for Companies
Tailored employee learning
Frequently Asked Questions
Can't find the answer you're looking for? Please reach out to our team.