Examples of Phishing Scams

Phishing Emails and the threat to PHI
Have you ever been working to clear out your email inbox and stumbled upon an email that either offered you a reward that seemed to good to be true or, on the other hand, tried to raise concern about an account being compromised? The chances are high that you were looking at a phishing scam email where the full intent of that message was for you to enter your personal information that a hacker could use to take advantage of you in some way. The potential cost of falling victim to these emails is one that is important to avoid!
A few months ago we shared an article all about phishing emails - including what they are, how to spot them in your inbox, and how to avoid them in the future. Phishing emails are not a new scamming method by any means, however, they are also not a tactic that is going away anytime soon. The specifics of a phishing email can vary from hacker to hacker, however, seeing some examples may help you to better spot them in your own inbox.
Example #1
Here is an example of a phishing email that I recently received as well as the clues that told me that this was an email to report rather than trust. This example represents one of the common themes of phishing scams - a false alert regarding a problem with one of your accounts. Keep an eye out for this method!
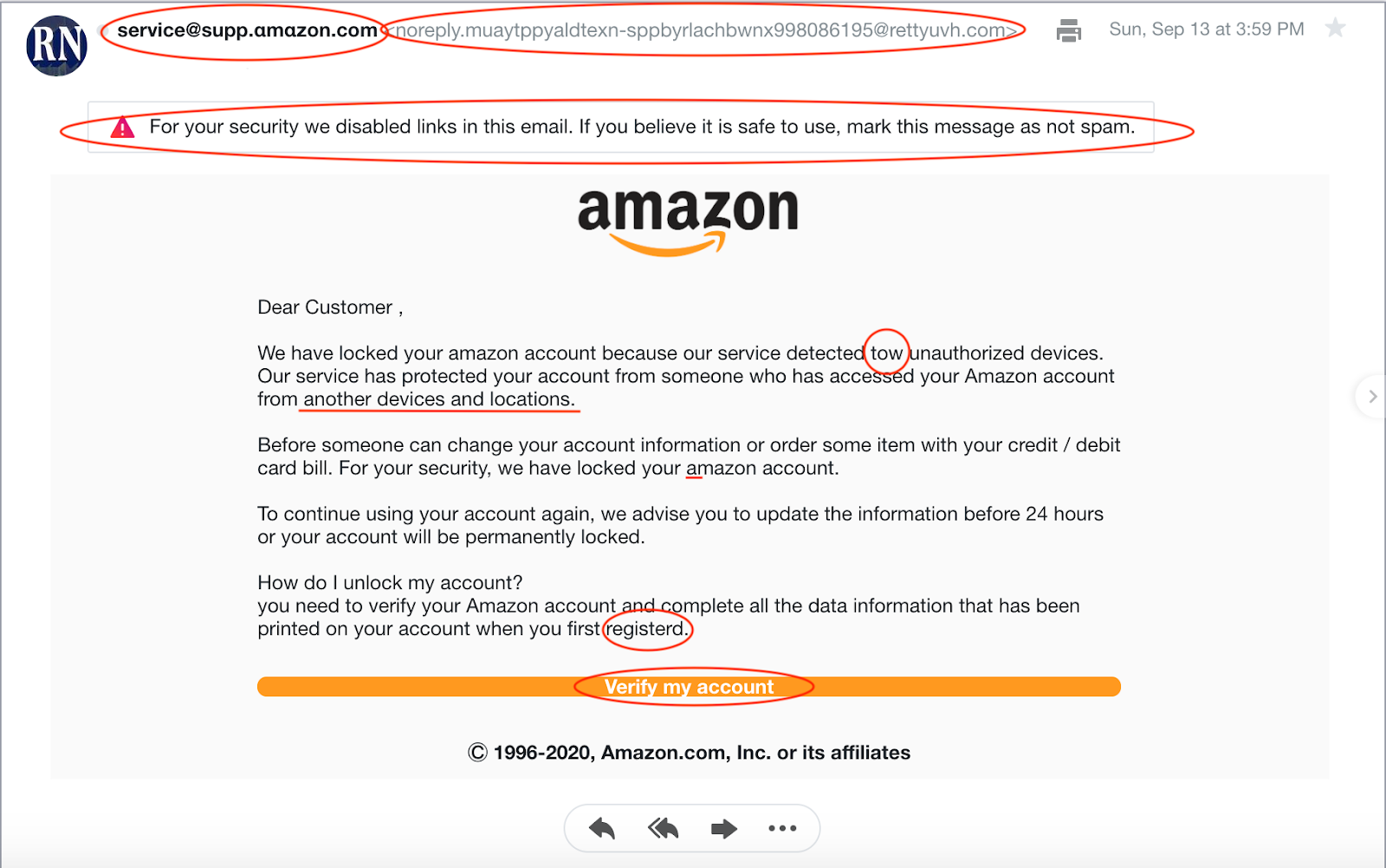
The first red flag for this scam email message was that it was sent to the wrong email address, meaning it was not sent to the one that is even attached to my Amazon account. Next, the sender address and reply address contain a variety of extra characters and words that legitimate company domain email addresses from Amazon would never contain. My email provider made this a flagged message to alert me to the potential scam so that I could proceed with caution.
Throughout the body of the email, there were a variety of spelling and grammar mistakes such as writing “tow” where they clearly meant “two.” After receiving training on phishing emails, all of these factors made it clear to me that this was not a reputable email from Amazon, but rather that it was an attempt at a phishing scam. Plus, based on the information I learned through this blog, I am well aware that scare tactics are one of the most common ways to attempt a phishing scam.
In this first example email above, the mistakes that the hacker made were clear and sprinkled throughout. However, there are certainly times that there will not be nearly as many or as clear of errors to notice. That is why you should always have a critical eye on all the details of an email before ever giving your information as requested.
Ready to simplify HIPAA compliance?
Join thousands of organizations that trust Accountable to manage their compliance needs.
Example #2
This second example features another popular method of phishing scams - advertising that the individual has won a prize or gift card but simply needs to input their information to receive this. Many people have experienced this form of scam through a pop-up advertisement on a website but it can easily be translated into an email phishing scam instead.
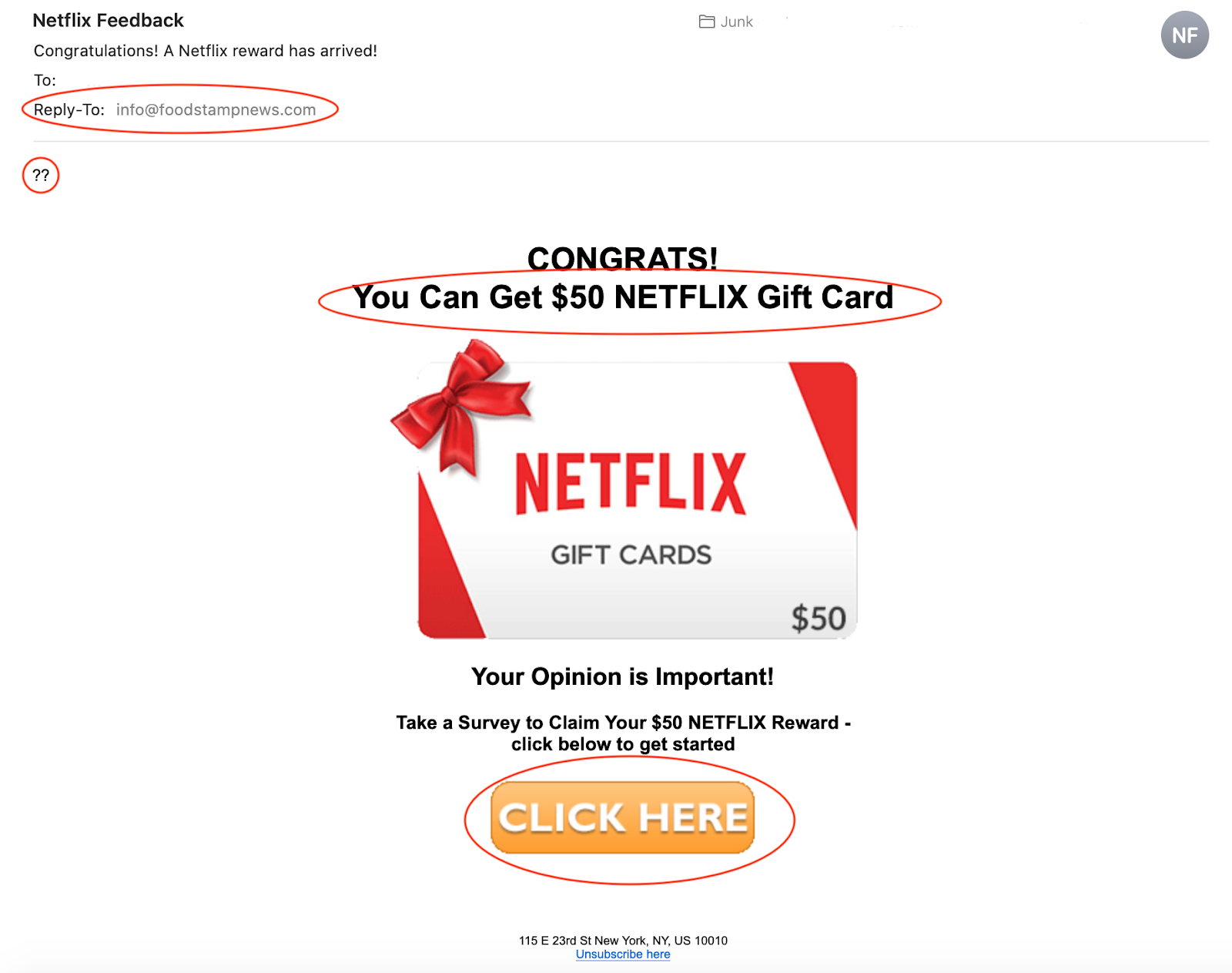
Although everyone would be happy to receive a $50 gift card to a popular streaming service like Netflix, there are a few red flags within this email that should alert you to the fraudulent nature of this message. First, the email claims to be sent to me from Netflix, however, the “reply-to” and sender email address is info@foodstampnews.com which is definitely not the account through which a legitimate email from Netflix would come.
Just as we mentioned with the first phishing email example, errors in spelling and grammar are extremely common in these scams. In this specific email, the main headline reads “You Can Get $50 NETFLIX Gift Card” which contains both improper grammar and haphazard capitalization. In addition this message is not addressed to me but rather the only body text is simply two question marks. Any legitimate corporate email would contain some form of introduction or greeting to the recipient. This helps to show us that a corporate marketing team is likely not responsbile for creating and sharing this email.
Lastly, it is always important to use common sense and err on the side of caution when receiving an email message that could be fraudulent. In this case, it is fair to assume that if Netflix were actually requesting surverys from their customers in exchange for gift cards, that this would occur through the actual Netflix account.
How to Report a Phishing Email?
When you are going through the messages in your email account, please be sure to report messages as phishing emails if you identify them as such.
The exact method of reporting a phishing email will vary a bit depending on what email provider you use. If you are a Gmail user, to report a message as a phishing scam, first open the message. Next, near the reply button, there will be three dots aligned vertically, click on those. In that drop-down, you will see “Report Phishing.” This will trigger a pop-up window that will explain what phishing is and then prompt you to report that message if you believe that it fits with the definition. Keep in mind that this will send the entire message to Gmail for them to investigate it.
Aside from Gmail, other providers offer similar methods for reporting potential phishing emails. Read more here about how to report suspicious emails through popular platforms like Microsoft Outlook and Hotmail.
HIPAA & Phishing Emails
With phishing emails just as with other forms of hacking or information-seeking scams, healthcare organizations are typically one of the first groups to be targeted. That is simply because the information that HIPAA organizations hold is more valuable to these hackers than that of many other industries. That is just one of the many reasons that the standards for information protected and security are extremely high under the HIPAA requirements.
Whether you are the privacy officer for a HIPAA compliant organization or just an employee that needs to work in compliance with the regulation, you may know that email presents a challenge to you. Email is an important tool for all organizations to use in order to communicate quickly and efficiently with teams and coworkers. However, in order to be able to utilize email in the most secure yet effective way, HIPAA-compliant organizations need to reach certain standards of encryption. Find out more about to configure your email security in conjunction with the HIPAA regulations here.
Table of Contents
Ready to simplify HIPAA compliance?
Join thousands of organizations that trust Accountable to manage their compliance needs.




